Fatih Yurtsever*
Chinese cybersecurity firm NSFOCUS has released a report detailing cyber attacks by a new advanced persistent threat (APT) hacking group called Muren Shark that is targeting Turkish defense industry projects. The report details which institutions and defense industry projects in Turkey were targeted by the hackers.
In recent years the Turkish defense industry has developed important projects, such as the production of armed unmanned aerial and surface vehicles and underwater and surface or underwater combat management systems. It has become necessary to protect critical storage information systems from cyber attacks and create information security. How well are critical institutions such as the Scientific and Technological Research Council of Turkey (TÜBİTAK) and the Turkish Naval Forces Command, which are main components of the Turkish defense industry ecosystem, protected from cyber espionage and cyber attacks, and how well are the personnel of these institutions trained in cyber security?
Muren Shark APT hacking group
Muren Shark is a new threat entity active in the Middle East, primarily targeting Turkey. Identified targets include TÜBİTAK and the Turkish naval forces. Muren Shark’s main attack techniques include the transmission of phishing documents and online attack services for direct purposes, including the expansion of attack resources, infiltration of target networks and theft of critical data. The organization’s known cyber attacks first surfaced in April 2021 with the intrusion into university websites. Muren Shark has done a good job of hiding attacker information in the activities it has conducted, and its geographic affiliation has not yet been confirmed.
The most recent round of Muren Shark activity occurred in early August 2022, when the attackers delivered in various forms of Turkish phishing documents to attack specific targets in Turkey. The phishing documents that appeared in this round of attacks have the following file names:
 Phishing attacks
Phishing attacks
Documents leaked or obtained from TÜBİTAK and the Turkish Navy were used in the phishing attacks. It is still unknown how the hackers obtained these documents.
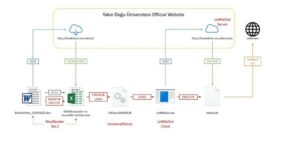
The process employed by the cyber attacker is very interesting. Muren Shark chose Yakın Doğu College in northern (Turkish) Cyprus as the main target of its cyberattacks. They infiltrated the college’s website and used it as a command control and data transfer server for precisely one year. Through this server, they sent the stolen documents from their infiltrated networks to the predefined points. They tried to cover their tracks to avoid detection during the attack; therefore, their identities and locations could not be determined.
Hackers embedded secret spyware into two documents that they had previously obtained for the phishing attacks. They then emailed these documents with the spyware embedded to employees of both institutions as if they came from TÜBITAK and the Turkish Naval Forces Command. When the employees who receive the email click on the document attached, the spyware is downloaded to their computers. Now the Trojan spyware is ready to run secretly on the target computer.
 Conclusion
Conclusion
As the information published in the report shows, the Muren Shark APT group used cyber espionage to obtain information about the Integrated Combat Management System (MÜREN), which was developed at the national level and intended for use in submarines. Unfortunately, this incident shows that the cyber defense capabilities of state institutions involved in the development of defense industry projects, such as TÜBİTAK and the Naval Forces Command, are not at the required level. The personnel working at these institutions are not adequately trained in cybersecurity. Turkey is a country that is at the center of cyber espionage activities due to the important projects it has developed in the defense industry in recent years. First of all, it should be clarified how the hackers got the two documents they used in the phishing attacks, and it must be precisely determined which documents the hackers captured in the cyber attacks. Cyber defense measures should be reviewed at TÜBİTAK and the Turkish Navy, and personnel should be trained on this issue.
* Fatih Yurtsever is a former naval officer in the Turkish Armed Forces. He is using a pseudonym out of security concerns.



